1 System Overview This design utilizes the powerful computing power of the DSP development board to implement a variety of information security algorithms that require a large number of operations. It realizes boot user authentication, voice confidential communication [1][2], text information encryption transmission, information hiding transmission [3], frequency hopping communication [4], information security storage backup, timing lock machine and terminal destruction, seven security Features. The whole design is based on the ICETTEK-VC5509-A development board. The hardware part of the system is also equipped with wireless RF module nRF24L01[5], 8&TImes; 8 keyboard and 128 & TImes; 64 blue screen LCD. The chip ZLG7289B[6] is used for keyboard scanning management, and the liquid crystal driver adopts MEGA16[7] single-chip microcomputer. The whole system not only realizes high-quality secret voice communication, but also has good human-computer interaction function. The system uses the uncertainty of power-on to input password time, randomly generates the user's private key, and generates the session key through the Diffie-Hellman [8] key exchange system (ECC implementation). In order to improve the security and flexibility of secure communication, the system implements LSB[13] information for four encryption algorithms AES[9], RC5[10], IDEA[11], KASUMI[12] and configurable parameters. Hidden algorithm. We developed and implemented the USB driver [14], which enables the development board to communicate directly with the PC, which also provides convenience for information storage backup. In addition to this, the system can set the time for automatic lock-up. The signal transmission model of the whole system is shown in Figure 1-1. Figure 1-1 System Transfer Model 2 Scheme design and comparison The implementation of Option 2 is more complicated than that of Option 1. However, considering that the security of the second scheme is higher, and the scheme 2 ensures the security of the session key, the lifetime of the session key is effectively shortened, and the security of the communication is improved. In addition, the public key parameters can be updated periodically through the PC. In addition, Option 2 is more suitable for wireless mobile communication, which is in line with our design background, so we adopt Option 2. 2.2 Speech coding scheme Option 1: Use G.721 coding [15] [16]. It combines the differential signal of ADM with the binary code method of PCM, which is a better waveform coding. The complexity of ADPCM is low, and the compression ratio before and after encoding is 4 to 1. The main idea is to use the difference instead of the absolute value. Option 2: Open source speech codec based on code-excited linear prediction algorithm Speex [17] [18]. Speex is mainly for VoIP (Voice over Internet Protocol) voice communication on the Internet. Its main design goal is to provide high quality and low bit rate speech coding. Speex can compress narrowband (8kHz), wideband (16kHz) and ultra-wideband (32kHz) voice signals in the same bitstream; the compression ratio can be 16 to 1. Although Speex has many advantages, the Speex codec algorithm is complex, and the hardware configuration required to run the algorithm is high. The transmission code rate of the RF module we use is 2 Mbps, and the channel can fully guarantee the communication quality. In theory, the above two schemes are applicable. We implemented the codec of speex and G.721 on the DSP development board. The actual test found that the speex codec will bring a lot of delay, because the speex codec algorithm is more complicated. Although we have minimized the speex algorithm, such as: minimizing the complexity of the algorithm, setting the codec quality parameter to the lowest, turning off the VBR baud rate characteristic, turning off the perceptual enhancement feature and AEC echo cancellation. Can not solve the problem of large delay. In addition, speex codec requires a lot of floating-point calculations. The development board we use is the fixed-point DSP of TIC55XX series. It takes more time to implement speex codec. Furthermore, the minimum frame length that speex can encode/decode. It is 160 samples, so it will bring a lot of delay to the system. G.721 codec can realize basic voice communication, but the communication quality is general. Considering that the system uses voice signal as the carrier of information hiding, the hidden information cannot be restored after the speech codec, so we finally choose PCM coding. Figure 4-1 Hardware architecture diagram 4.1.2 RF Transceiver Module Figure 4-2 Circuit diagram of the RF module       Â
Fiber Optical Distribution Box(Metal) Fiber Optic Distribution Box is specially designed for FTTH or FTTB for Indoor/Outdoor application. It is can manage single,ribbon & bundle fiber cables. It consists of splicing, distribution and panel with ensures the excess fiber cords and pigtails in good order, no interval and easy for management and operation. It offers mufti-functions of distribution management.
Indoor Fiber Optical Distribution Box(Metal) Indoor Fiber Optical Distribution Box(Metal),Fiber Optic Distribution Cabinet,Metal Electrical Boxes,Metal Equipment Cabinet Sijee Optical Communication Technology Co.,Ltd , https://www.sijee-optical.com
2.1 System Security Solution
Solution 1: Pre-key, regularly change the key, and encrypt the data with a symmetric cryptosystem. The PC pre-sets the key to the terminal through the USB, and uses the preset key for symmetric encryption during communication. The security of the system depends to some extent on the update period of the key, but in practical applications, shortening the update period of the key is troublesome.
Solution 2: Key exchange is based on public key cryptosystem, and data encryption is based on symmetric cryptosystem. The PC writes the parameters of the public key algorithm to the terminal through the USB. After booting up, A and B randomly generate their own private key, calculate their own public key, and disclose their public key to the other party. A uses his private key and B's public key to generate a session key. B generates a session key through his private key and A's public key, and the session key is the same. After the communication ends, the generated private key, public key and session key are cleared, and the process of generating the session key is repeated next time the power is turned on.
4 system implementation
4.1 Hardware implementation
4.1.1 System Hardware Architecture
The hardware architecture diagram of the terminal is shown in Figure 4-1. It is mainly composed of ICETTEK-VC5509-A evaluation board, nRF24L01 RF module, 128&TImes; 64 LCD, 8×8 keyboard and MEGA16 MCU control module. 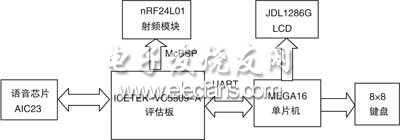
The RF module uses nRF24L01, and its circuit diagram is shown in Figure 4-2. 
